Cybersecurity is a topic near and dear to most business owners’ hearts. You might not specialize in securing your infrastructure, but it’s still a vital factor that cannot be ignored. Today, we want to cover how you can make cybersecurity as easy as possible for your team so they don’t accidentally put your business at risk.
Washington Works Blog
Unless they run a technology company, business owners shouldn’t have to give much thought to their network protection. They have much more critical things to spend their focused time on. Unfortunately for them, cybersecurity is extremely important, so having an ongoing strategy to consistently upgrade your network defenses is something most businesses should consider. Today, we thought we’d go through six reasons you need to take network security seriously.
Let’s imagine that your business has a hidden back door—one that your building manager doesn’t even know exists—and that door leads straight into the heart of your office. By the time someone finds out that door exists, someone could have snuck in to wreak all kinds of havoc, unbeknownst to you. This is what is known as a zero-day threat; it’s a security vulnerability that is being actively exploited in the wild, one that was previously unknown to the vendor and unpatched against, and it’s a serious problem for any SMB.
When considering the strengths of shapes, the triangle is generally considered the strongest, its three vertices creating the optimally stable configuration. The same can be said of your business’ approach to cybersecurity. The difference is that, instead of three equal legs working together to support whoever is seated on a stool, your business’ cybersecurity relies on equal investment in three key areas: your people, your processes, and your technology.
Let’s talk about how this holistic approach puts your business in the best position to stay secure, and where many organizations fall short.
Cyberattacks aren’t just some far-off headline problem, they’re a real threat to businesses, individuals, and even governments. Hackers are smart, sneaky, and relentless. Fortunately, developing a few smart habits can make it really tough for hackers to mess with you. In this month’s newsletter, we’re breaking down how you can level up your security game and stay off a hacker’s radar.
Imagine leaving the physical doors of your business unlocked overnight. The thought is unsettling, isn't it? You wouldn't risk your assets, your hard work, and the trust of your clients like that. That's precisely the risk many small to medium-sized businesses (SMBs) unknowingly take by underestimating the importance of cybersecurity.
Let’s explore just how important proper cybersecurity truly is.
With remote workers, you have a lot more questions to consider on a daily basis, especially in the realms of productivity and security. If you’re not careful, you could put your business at risk. Here’s how you can face these challenges head-on and ensure your organization doesn’t suffer any negative side effects of remote work.
Have you ever thought about whether a hacker could secretly read your emails with your clients and coworkers? If you handle your own email system, it's really important to know about email encryption. Encryption helps keep your emails safe and private so you can focus on running your business without worrying about hackers.
Here are three big problems you could face if you don’t encrypt your emails:
Cybersecurity is a major part of business computing today, mainly because there are so many threats. Cybersecurity professionals and network administrators must innovate to confront these threats. This month, we thought we would review three of these innovations to give you an idea of what is being done to help businesses handle the rough-and-tumble cybersecurity landscape.
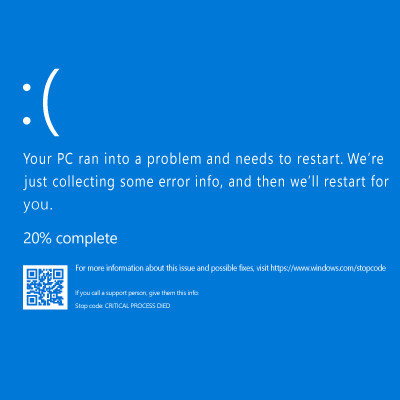
July 18th, 2024 saw one of the most widespread and devastating outages in recent memory, as a global update from cybersecurity company CrowdStrike brought about significant impacts to major infrastructures and societal needs. All this occurred even though only 1% of Windows operating systems experienced the issue.
Technology is integral to modern business, making proficiency in necessary tools a must for today’s workforce. However, the complexity of these technologies can create vulnerabilities as malicious actors continually seek ways to infiltrate systems, steal data, and siphon funds.
Firewalls are stalwarts in network security. They serve as a protective barrier between trusted internal networks and potentially hazardous external ones, such as the vast expanse of the Internet. Essentially, they act as vigilant gatekeepers, scrutinizing each packet of data attempting to traverse their domain. Let’s briefly discuss the diverse types of firewalls and their pivotal roles.
Are you prioritizing your business’ network security? It’s remarkably important that any modern business focuses its efforts on this aspect of running a company. Still, it can be challenging to implement the right tools for the job—particularly if you are a future-minded business. You want to get the best return on your investment, which makes sense. Let’s help you get there.
Chances are your business has a social media presence in at least some capacity, as it’s a good way to drive traffic to your business. However, hackers want to leverage this benefit against you. A new malware specifically targets Facebook business accounts to launch malicious advertisement campaigns using your own money against you.
It’s important to keep the software on your computer updated. If your operating system or web browser or some other important application is out of date, it could lead to things not working properly while also leaving you susceptible to threats. However, hackers are disguising malware to look like important web browser updates.
Cybercriminals fight dirty, whether it’s attacking small businesses, large enterprises, or individuals who just want to watch Netflix. It doesn’t matter who you are or what you do for the community; you’ll always be a target for hacking attacks. To save time and effort, hackers will use low-tech attacks and social engineering attacks to target individuals. Hackers aren’t developing new threats all the time; if anything, they largely use existing exploits, purchasable software, and social engineering to take advantage of people.
As the threat landscape gets more concentrated with serious cyberthreats, new next-generation firewalls (NGFWs) have been developed to help stem the tide of negative outcomes that result from cyberattacks. An NGFW is an advanced network security device or software solution that combines traditional firewall capabilities with additional features and functionalities designed to provide enhanced protection and visibility into network traffic. NGFWs are designed to address the evolving and sophisticated nature of cyberthreats, including malware, intrusion attempts, and other malicious activities.
Any business that depends on its IT—in other words, most businesses—needs to consider the cybersecurity that is in place to protect it. Today, many businesses have started focusing their cybersecurity efforts on protecting their network from the edges, an approach that is fittingly known as edge security. Let’s take a moment to talk about the benefits that edge security can offer you.